Your Android Device Is Not As Secure As You Think It Is
Smartphones get stolen every day, we all know this, and we all have the little things we do to “protect” the extensions to our arms. We all grip our phone harder when a second person joins you at the bus stop, we all check our perimeter every time we unlock our phone, we all got that taser case for our Galaxy S3… Ok, maybe that’s just me but that taser is pretty sweet. The point is, we try to take steps to protect our $600 devices, we put passcodes on them, we install tracking/wiping applications like Lookout, but I’m going to explain why most of that truly won’t protect your device if it gets stolen.
Let’s start off with a sample scenario. You’re waiting for a bus and you check your phone for some Facebook messages. You realize your bus is on the way and you quickly stand up. Your phone falls out of your pocket, but it’s only until you’re on the bus and long gone that you realize that you’re Android smartphone is no longer with you. But no worries, your device has one of the many Device locators installed (such as Lookout), but unfortunately all of these services rely on one simple fact: that your device is still connected to the internet. So what are you supposed to do?
According to Google… Nothing. That’s not good! Unfortunately most Android devices have a feature where you can place a device in Airplane mode by simply pressing the power button until a menu pops up (allowing you to shut off the device, reboot, airplane mode, etc.). For example with the bus stop kerfuffle; If a thief were to steal your phone from a bus stop, they could easily take your device and place it into airplane mode, and thus, all your attempts to destroy your pictures of cats have become futile. But you’re smart, you have Cerberus, or Lookout, or one of the many other Device Protection apps installed. Unfortunately, very few of them prevent against failed passcode entry attempts and if your device is in Airplane more, you’re screwed. That means you can’t remote lock or wipe your device and that your device and all its lude cat photos are in the hands of an attacker… even if it’s encrypted. So what are you to do if an attacker Brute Forces your PIN using inexpensive software/hardware, like I did with the Arduino-based DigiSpark?
[youtube http://www.youtube.com/watch?v=Weyvg3E7kEc]
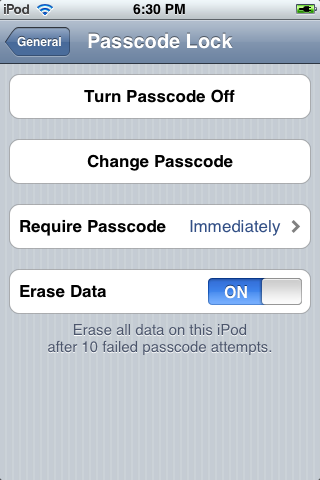
The answer is not much… Google needs to allow users to enable a little setting that will automatically wipe the device after a number of failed attempts– similar to iOS.
iOS allows users to have their data wiped after 10 failed attempts. This should be more than enough for you to stop your cat from accidentally wiping you phone while swatting at the lock screen and way too few attempts for someone to unlock your device like I did in the video. However, this is only one part of our bus stop thief problem. It still doesn’t address the fact that they can simply put the phone into airplane mode in less than 5 seconds… and they’re not even on an airplane… silly thief. If a bus stop thief wanted to prevent you from locking/locating/wiping your device remotely, all they would need to do is simply place your phone in “airplane mode.”
The solution should be pretty simple: Android needs to require you to enter your passcode before entering airplane mode. It’s not often that a user would find themselves unable to place their own device in airplane mode and forget their own unlock code.
So until Google fixes these two issues, follow this advice:
Use a security app, such as Cerberus, that will wipe your phone after a number of failed unlock attempts. This should be a temporary fix until Google adds this functionality into the OS itself. As for airplane mode… we’re all kind of out of luck, there’s not much we can do to protect against that.
Hopefully now, you’ve become paranoid like me after reading this article and you’ve already started looking for that taser case for the Galaxy S3 on Amazon… I may or may not have made that up.






It’s a good point. It reminds me of years ago when I was a systems admin, I thought on Windows Servers really ought to require a password. (Coming to work with a hangover…oops….just accidentally shutdown the Exchange server when I meant to ‘Log off’ 😉
That’s strange, my message got truncated. I was talking about a password in order to shut down a server.
The air plane mode setting can be disabled in settings. Not the setting itself, per say, but the ability to turn it on from the lock screen. This solves the issue of a thief disabling tracking.
Preventing people without the passcode from entering Airplane Mode doesn’t do any good. The problem is that even if they did that, there’s nothing preventing the thief from *turning the device off*. At that point, they pop the SIM card (no more Internet), and break in as usual. And if your phone is rooted, unlocked, or has USB Debugging enabled, they don’t even need your passcode to get into it.